Cybersecurity researchers disclosed four flaws in Microsoft Teams that could let attackers manipulate chats, impersonate colleagues, and change notifications to hide who really sent a message. Some issues were fixed in 2024 under CVE-2024-38197, with additional patches in September 2024 and October 2025. The core risk is simple: attackers could erode trust in internal communications and trick people into clicking links or sharing sensitive data.
The Short Version
- Four Teams vulnerabilities enabled message manipulation, silent edits, and spoofed identities.
- CVE-2024-38197 covers a spoofing issue, rated medium severity (CVSS 6.5), affecting Teams for iOS.
- Fixes rolled out in phases across late 2024 and October 2025, after disclosure in March 2024.
- Risks include social engineering, phishing, and convincing fake requests that look like they came from executives or IT.
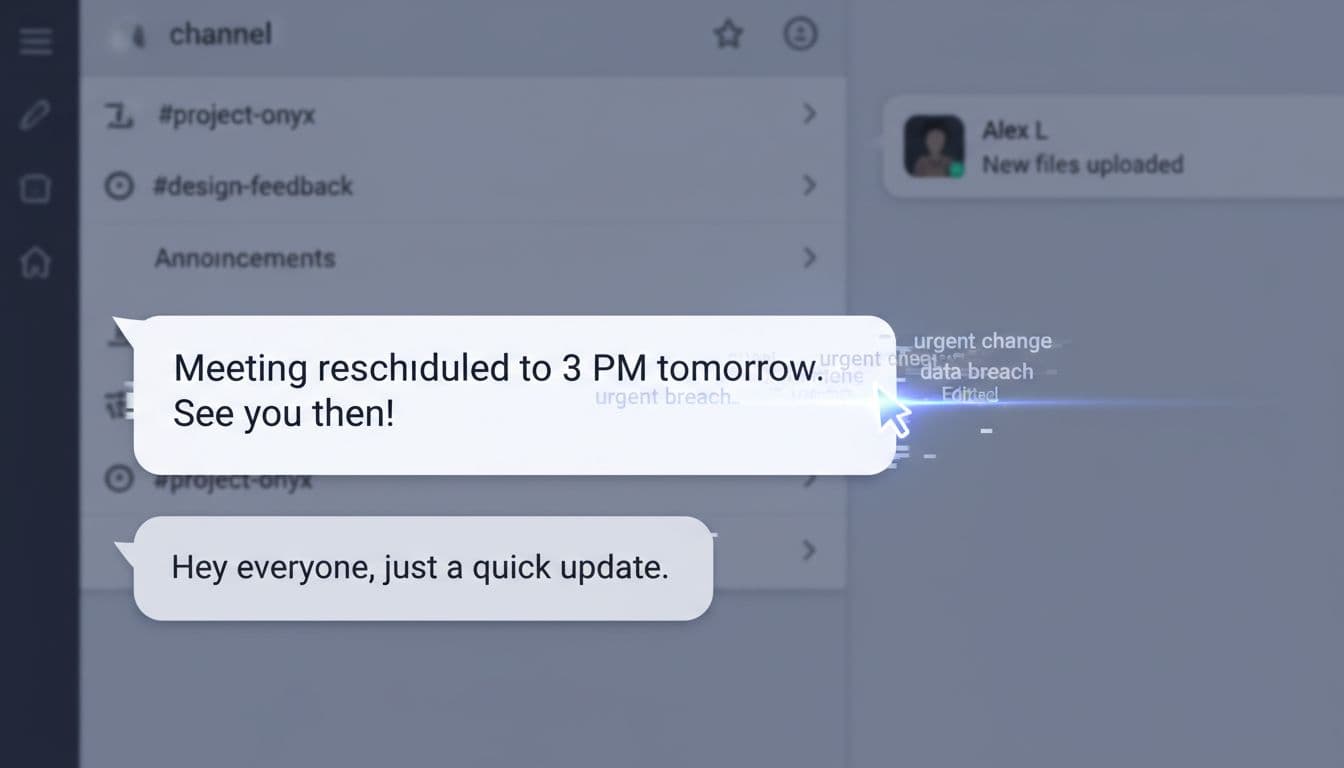
What The Flaws Allowed
According to Check Point’s research shared with The Hacker News, the bugs made it possible to:
- Edit messages invisibly: Alter content without the “Edited” label, masking changes.
- Spoof sender identity: Modify notifications so messages look like they came from someone else, even high-profile leaders.
- Forge display names: Change names in private chats by editing the conversation topic.
- Spoof calls: Modify display names in call notifications and during calls to forge caller identity.
These attacks could be used by external guest users or malicious insiders. The outcome is the same: users may trust a fake request and take risky actions.
Microsoft’s Response
Microsoft addressed parts of the findings starting in August 2024 with CVE-2024-38197, and continued rolling out fixes through September 2024 and October 2025. The company has warned that Teams’ broad feature set and global adoption make it a prime target. Threat actors exploit chat, calls, meetings, and screen sharing to coax users into granting access or running payloads.

Why This Matters
Business messaging tools carry trust. People assume a message from a colleague is real. If attackers can change names, edit messages silently, and spoof notifications, they can run high-quality scams. Think fake wire instructions, urgent HR requests, or IT prompts to install a tool for a “meeting.” Even cautious employees can be fooled when cues look authentic.
Practical Steps For Teams Admins
- Update everywhere: Ensure Teams apps are current on desktop, web, iOS, and Android. Enforce updates where possible.
- Tighten external access: Review guest policies, external federation, and who can DM or call users from outside the tenant.
- Harden notifications: Encourage users to verify sensitive requests in-app rather than relying on toasts, emails, or push previews.
- Conditional Access + MFA: Require strong authentication and device compliance before access to Teams and files.
- Disable risky add-ons: Audit third-party apps and bots connected to Teams; remove those you don’t need.
- Data protection: Use DLP to flag or block sensitive data in chat and files; log events for incident response.
- Least privilege: Limit who can create teams, invite guests, or manage org-wide settings.

Employee Safety Checklist
- Verify identity for sensitive asks: If someone requests money transfers, credentials, or files, confirm via a second channel.
- Watch for edits: If a message changes content mid-thread, pause and re-verify before acting.
- Hover and check links: Open links from the Teams app, not from notification previews; check the domain carefully.
- Report fast: Use your org’s phishing or security report button in Teams, or alert IT immediately.
- No credentials over chat: Never share passwords or MFA codes in messages or calls.
Detection And Response Ideas
- Alerting: Monitor unusual spikes in external DMs, new guest invites, or account behavior changes.
- Audit logs: Centralize Teams audit data into your SIEM; create rules for identity or display-name anomalies.
- Link detonation: Route URLs through safe-link rewriting and sandbox testing where available.
- Playbooks: Prepare incident steps for suspected Teams impersonation: disable affected accounts, revoke sessions, and broadcast advisories.
- Training: Run phishing simulations and short refreshers focused on collaboration-tool scams.
For Content Creators And IT Communicators
Turn this into helpful internal comms and public content:
- Post a short explainer: “How Teams Spoofing Works And How To Stay Safe.”
- Create a one-page checklist for employees with the safety steps above.
- Record a 60–90 second video that shows where to verify senders and report suspicious chats.
- Update your acceptable use policy to ban sharing secrets in chat and require secondary confirmation for sensitive actions.
Collaboration tools are a prime attack surface. These Teams flaws show how message edits and identity cues can be abused to run convincing scams. Keep clients updated, restrict external access, and teach employees to verify sensitive requests in-app. With layered controls in place, you can reduce the chance of a spoofed chat turning into a costly breach.
To contact us click Here .







